
Block Outgoing Traffic to Private Networks
Introduction Recently I got an email from the network department of my provider, letting me know that they had indications that one of my servers

Introduction Recently I got an email from the network department of my provider, letting me know that they had indications that one of my servers

1. Introduction In this tutorial, we’ll introduce the Unix swap space, its advantages, and a few simple commands to manage it. 2. The Unix Swap

Overview Delve into an In-depth guide on crafting bootable USB drives in Linux using the dd utility and Ventoy. This tutorial provides step-by-step instructions, ensuring

Introduction: Secure Socket Tunneling Protocol (SSTP) is a robust VPN protocol utilizing SSL/TLS encryption, designed by Microsoft to enhance security and simplicity. This guide walks
Introduction: Ever wondered why you can only use half of your SSD or HDD storage? The answer lies in RAID, or Redundant Array of Independent
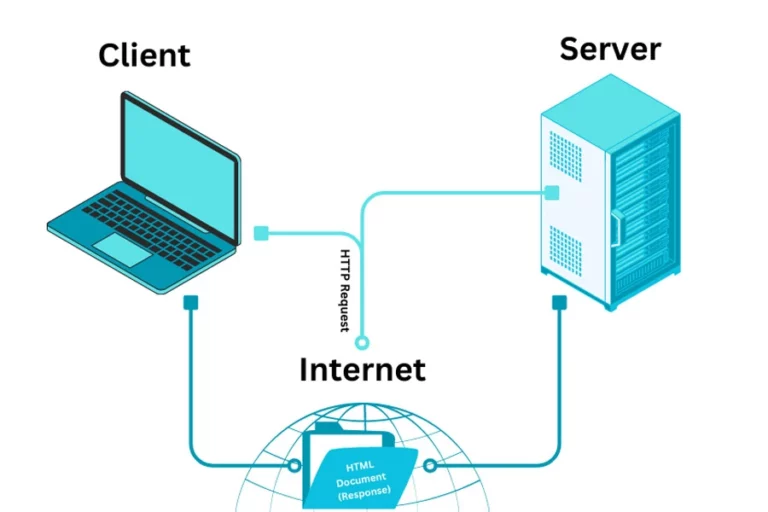
In the ever-evolving digital landscape, mastering the intricacies of Linux web servers is key to unlocking the full potential of your online presence. This comprehensive
With the latest release of Ubuntu, I thought it would be the perfect time to talk about server upgrades. Specifically, I’m going to share with

If you’re here to resolve an unintended recursive chmod or chown command on an RPM-based Linux system, follow this quick solution with root privileges: rpm

SSH tunneling, a fundamental aspect of secure shell client utility in Linux, allows for establishing secure connections to remote or local SSH servers. While some
Introduction: This article provides an overview of fundamental Linux filesystem concepts without delving into specific file system types like EXT4. It aims to clarify the