Category: Linux
-

Linux USB Mastery: In-depth Guide with dd and Ventoy
Overview Delve into an In-depth guide on crafting bootable USB drives in Linux using the dd utility and Ventoy. This tutorial provides step-by-step instructions, ensuring a seamless experience from start to finish. 1. Using dd for a Single-Boot Drive 1.1. Initial Checks Before commencing the process, perform initial checks using the ‘lsblk’ command to identify…
-

Setting Up an SSTP Server on Linux with SoftEther VPN
Introduction: Secure Socket Tunneling Protocol (SSTP) is a robust VPN protocol utilizing SSL/TLS encryption, designed by Microsoft to enhance security and simplicity. This guide walks you through configuring an SSTP VPN server on Linux using the versatile SoftEther VPN. What Is SoftEther VPN? Discover SoftEther VPN, an open-source, cross-platform VPN implementation by the SoftEther VPN…
-

Linux Server Upgrade Guide: Pro Tips with Commands
With the latest release of Ubuntu, I thought it would be the perfect time to talk about server upgrades. Specifically, I’m going to share with you the process that I’m using to perform upgrades. I don’t shy away from work, but I hate doing work that really isn’t needed. That’s why my first question when…
-

Fixing File Permissions on RPM-Based Linux Systems
If you’re here to resolve an unintended recursive chmod or chown command on an RPM-based Linux system, follow this quick solution with root privileges: rpm –setugids -a rpm –setperms -a The –setugids option sets user/group ownership, and –setperms sets file permissions. If successful, great! For thoroughness or unresolved issues, read on. Why Fix Permissions and…
-

Linux SSH Tunneling: Port Forwarding Guide
SSH tunneling, a fundamental aspect of secure shell client utility in Linux, allows for establishing secure connections to remote or local SSH servers. While some programs may be inflexible in processing via SSH due to their design limitations, SSH offers multiple options for redirecting secure traffic to accommodate such scenarios. Let’s explore various cases and…
-
Understanding the Fundamentals of Linux Filesystems
Introduction: This article provides an overview of fundamental Linux filesystem concepts without delving into specific file system types like EXT4. It aims to clarify the purpose of storing data on hard drives and introduces the basic principles of Linux filesystems. Why Data Storage on Drives is Essential: Computers need to store data on hard drives…
-
Mastering Linux Firewall: IPTables Setup & Commands Guide
When setting up a firewall in Linux, it’s essential to understand the basics of how it functions and the commands involved in configuring it. The guide below provides insights into the working of the Linux firewall and the fundamental commands to establish and manage rules using IPTables. What is a Firewall? A firewall acts as…
-
10 Reasons to Learn Vim: The Advanced Text Editor
10 Reasons to Embrace Vim Text Editor Vim, born from the union of Vi and “improved,” represents a powerful text editor entrenched in history. Here’s a concise exploration of why learning Vim could significantly elevate your text editing experience: Ubiquitous Vim Access on Every System: Vim’s omnipresence across systems, especially in Linux distributions, makes it…
-
Installing an SSL Certificate on AlmaLinux
To properly install an SSL certificate on your AlmaLinux server running the Nginx web server, you’ll utilize Let’s Encrypt, a non-profit Certificate Authority (CA) issuing SSL certificates for free. The following step-by-step guide details the process, ensuring a secure connection to your domain. Background and Prerequisites Before initiating the SSL certificate installation process, ensure you’re…
-
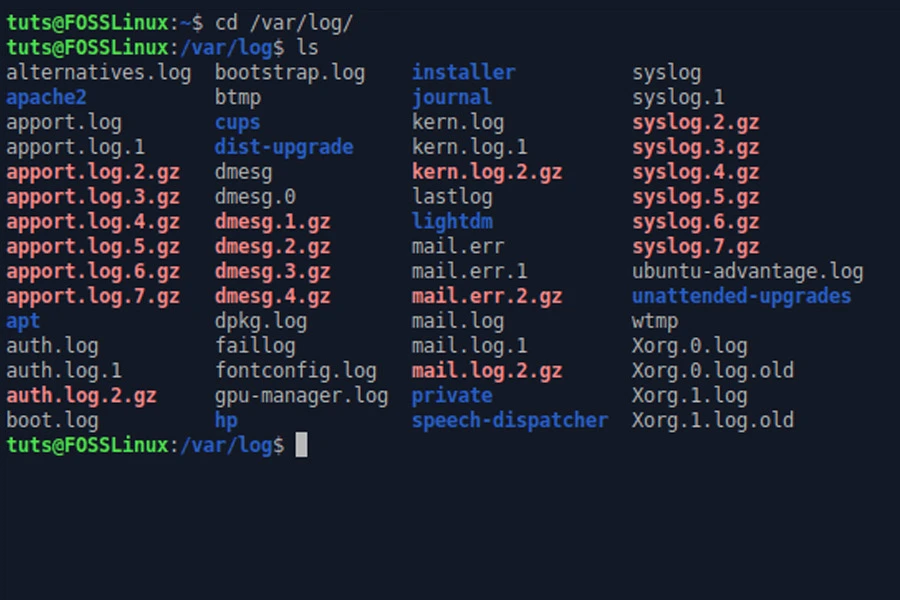
Analyzing Linux Logs: A Guide to Efficient Log Management
Managing Linux logs can be a goldmine of information, but extracting actionable insights requires the right tools and techniques. From command-line utilities to advanced log analysis tools, the process is essential for any system administrator to unravel critical system performance indicators and security incidents. In this segment, we’ll delve into a set of powerful tools…